
Last week, I attended the FinDEVr conference in New York City. The 2-day conference is focused on the technology aspect of fintech. Attendees ranged from financial institutions to data analytics startups coming from places like Canada, the U.K, and all across the U.S. At the conference, I gave a talk titled “Tapping Hackers for Continuous Security”.
Here’s a recap of the topics I addressed.
We come from a world where security issues were blamed on the developers. Introducing a security issue meant you wrote poor quality code. No wonder many developers dislike their company’s security team!
However, this landscape is changing. Modern developers realize they make mistakes. We’re human after all. It’s simply inevitable that you are going to introduce a security issue at some point. And that is totally okay! The modern software engineer embraces continuous development. With that also comes continuous security. Instead of waiting for a slap on the wrist by the pentesting firm your boss’s boss hired without you knowing, they get proactive about security.
Daily code commits call for a security solution that is continuous. At HackerOne, we call this Hacker-Powered Security.
There are two approaches to hacker-powered security.
-
The first is vulnerability coordination. It is essentially the same as Responsible Disclosure or Vulnerability Disclosure. Vulnerability Coordination is a more reactive approach where you publish a process that informs people outside of your organization what to do when they have discovered a potential security vulnerability in your systems. The U.S. Department of Defense calls this the “See Something? Say Something” of the digital world. You can also see it as rolling out the welcome mat for whitehat hackers.
Vulnerability coordination is rapidly becoming a requirement for compliance in many industries. Frontrunners include the automotive and healthcare industries, but we are in the early phases of a similar transformation in finance and insurance.
-
This second form, bug bounties, is a more advanced way to leverage Hacker-Powered Security. It can be seen as an extension to Vulnerability Coordination. However, with a bug bounty you are taking it to the next level by actively incentivizing the largest community of hackers to perform continuous security research on your products. You are literally offering cash rewards for hackers that turn in valid vulnerabilities.
An added bonus is that software engineers can actually learn about security via their company’s bug bounty program. Engineers will get exposed to practical examples of vulnerabilities that are real and exploitable. What a great learning resource!
If you’re doing penetration testing already, a bug bounty may actually help you save cost there. You are paying for results rather than time spent by one or two consultants from a security consulting firm. We often see customers laser-focus their penetration testing efforts based on the output of their bug bounty program. Maybe your bug bounty program reveals a particular app or property that is most vulnerable, and you can use these insights to focus your penetration tests, ultimately making them more efficient.
But more importantly, bug bounties are the cherry on top of the Software Development Lifecycle (SDLC).

Bugs start in development. Bugs also end in development. You feed bugs into the same cycle and follow all of the same steps to get them fixed. Quality Assurance (QA), automated or human, is part of the SDLC, and bug bounties are a form of QA. It allows you to have thousands of curious and creative eyes watching over your systems 24/7. You can see them as your friendly neighborhood watch.
If you develop agile and deploy often, maybe even as often as multiple times a day, you are going to need a security solution that is agile as well. Solely relying on quarterly penetration tests doesn’t cut it–the results will be outdated the minute a new code goes out out the door. Bug bounties are the agile form of security. With the right incentives, there are always hackers ready to take a crack at your systems.
If you take a look at the Continuous Delivery cycle, it has a dedicated test stage. While security should be covered there to the extent you can, with things like static code analysis and vulnerability scanning, it should be understood that it is not going to find everything. And that is why you need a continuous security solution that is a key part of your SDLC.
The most advanced bug bounty programs go the extra mile. They analyze the output of their bug bounty program and use these insights to make data-informed decisions in their day-to-day operations. The output of your bug bounty program gives you real-time insight into your security posture and helps focus and prioritize your efforts.
It can also help answer what trends are occurring. For instance, it could help you find that your app is most vulnerable to Cross-Site Scripting (XSS). That in turn could point to bad coding practices or the lack of a secure-default web framework.
In the chart below, it can help inform how effective your measures to fight against XSS are. Probably very effective, seeing that XSS is tapering off fast after July, while the average bounty for this type of vulnerability is going up. There’s no better proof that your measures are working than offering top-dollar for a certain class of vulnerability and receiving very little to no incidents of that type.
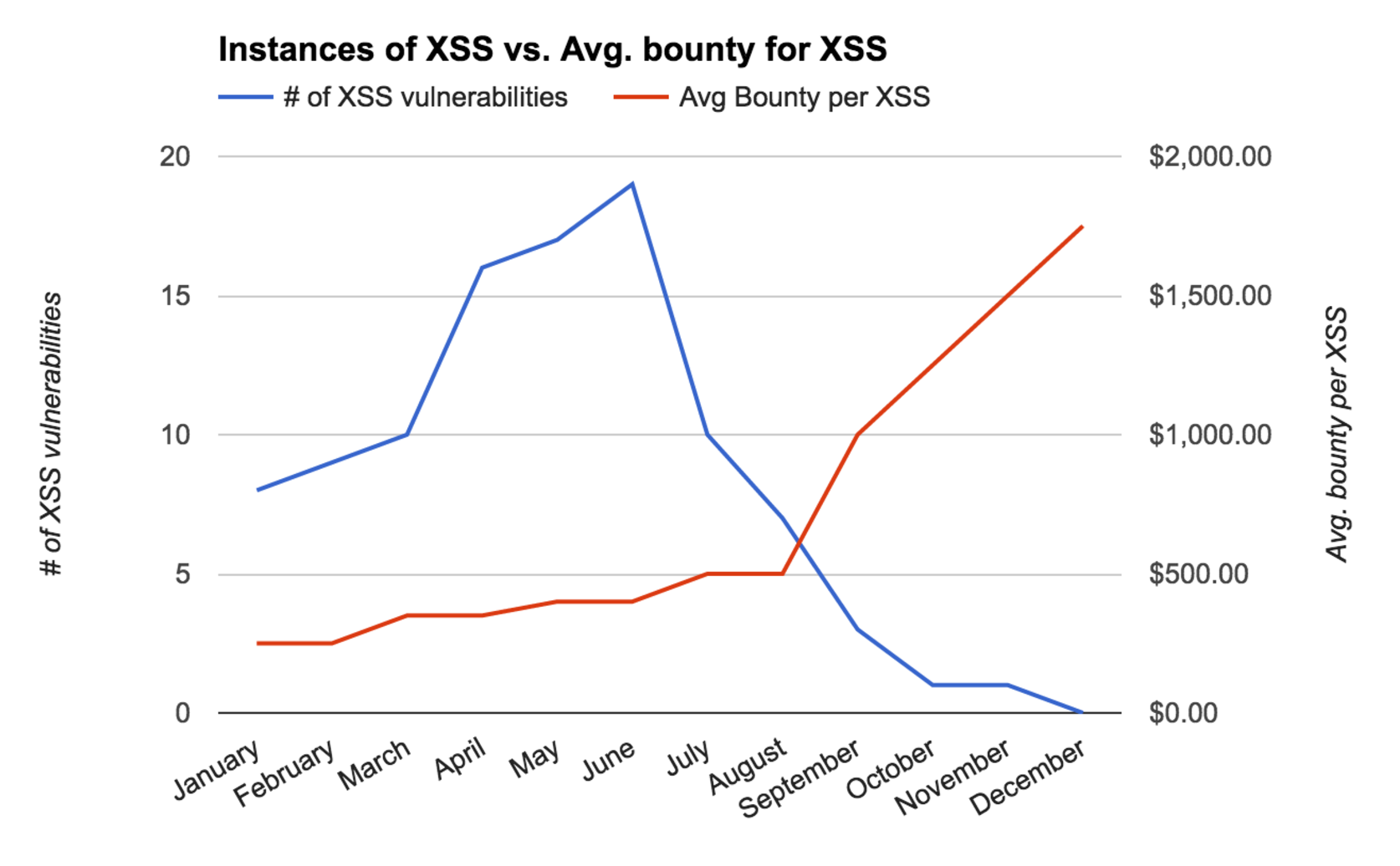
Even if your company doesn’t have a bug bounty program, many engineers from all around the world can still learn about security through practical examples of vulnerabilities other companies have suffered from.
At HackerOne we call this Hacktivity. It is a feed of publicly disclosed vulnerability reports. Other members from the community can upvote the best reports. Reddit-style.
Companies and hackers have the ability to choose to disclose any vulnerability report. Some will redact the salient information, but disclose the title and broad details of the report. Companies benefit from the extreme transparency towards their users. Hackers benefit from the fame of having helped a well-known company, and the interaction being disclosed allows them to demonstrate their skills publicly.
But more so, the entire world benefits by being able to learn from security vulnerabilities other companies have introduced. There’s no better way to learn security than by studying practical examples of past vulnerabilities others have suffered from!
The world is changing and it will take all of our collective efforts to address the legacy troubles, and stay ahead of the security issues of tomorrow. That’s why I believe in hacker-powered security – tapping into the collective genius of hackers will enable fintech companies and all companies to be more secure.
– –
HackerOne cofounder
Ps – see the full slide deck on slideshare
HackerOne is the #1 hacker-powered security platform, helping organizations find and fix critical vulnerabilities before they can be criminally exploited. As the contemporary alternative to traditional penetration testing, our bug bounty program solutions encompass vulnerability assessment, crowdsourced testing and responsible disclosure management. Discover more about our security testing solutions or Contact Us today.